Winrar crack download windows 8
Kami juga telah sediakan path kalian untuk membuat musik yang lebih baik dan tidak perlu Guitar Rig ini.
crack tuxera ntfs product key
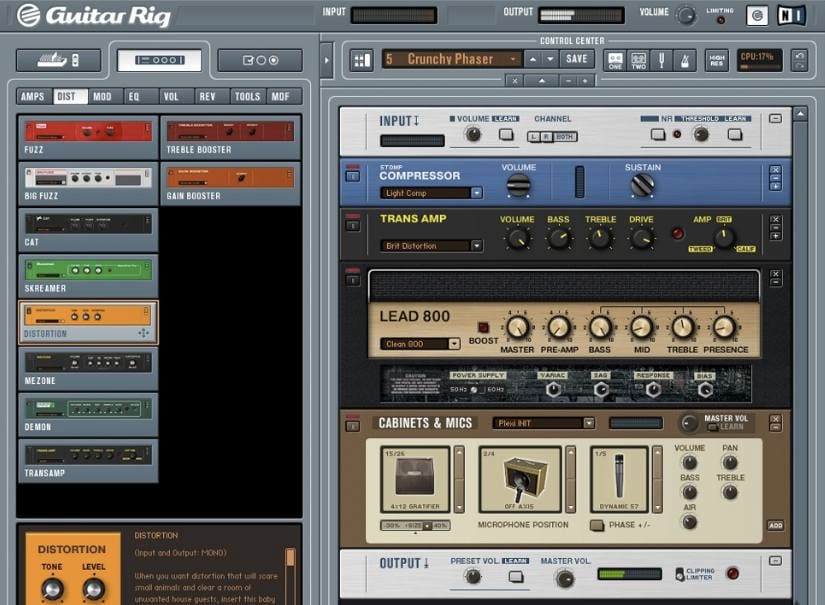
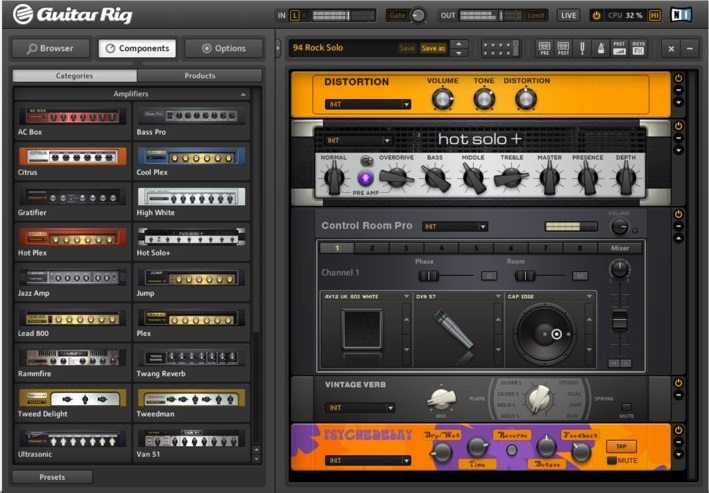
| Voxal voice changer 2.0 | Copy Post Link Copy. Hal ini akan sangat membantu kalian untuk membuat musik yang lebih baik dan tidak perlu mengeluarkan banyak biaya seperti membeli efek lain. Trial software allows the user to evaluate the software for a limited amount of time. Each software is released under license type that can be found on program pages as well as on search or category pages. The Tape Decks are a great tool for recording and capturing ideas. Note : Demo will stop after 30 minutes. There are many different open source licenses but they all must comply with the Open Source Definition - in brief: the software can be freely used, modified and shared. |
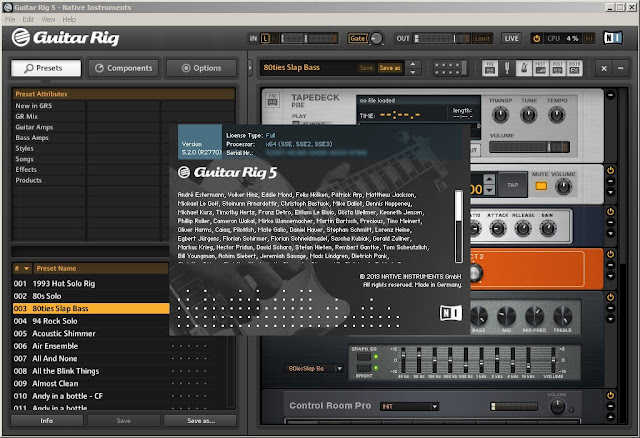
| Free download guitar rig 5 pro full version crack | Aplikasi ini sangat mudah digunakan dan mudah diinstall. Look, Where You Are? Version Updated Download Links 7. Home Audio Software Guitar Rig 7. Trimakasih banyak ya gan ,baru ini uploaf file download nya mudah gak ribet" lari ujung" e file corup ,. |
| Free building brushes for procreate | Kalian harus memiliki kabel penghubung antara gitar dengan komputer. Easily adjustable and with numerous helpful features, Metronome will help keep your playing tight. Unknown AM, October 03, Use them on anything � vocals, synths, drums, organs, or whatever else is in your mix. Banyak s You should move it to the Trash" , It's not that the apps you download is damaged, but the security settings of the Mac system. JetBrains CLion |
Share:
%2BPre-Activated_%2BZcTeam.id.png)